Although iPhone viruses are rare, there are certain kinds that do exist for iOS. If you suspect that your iPhone is infected with virus, then you must act quickly and take certain measures to make sure it is removed. Fortunately, there are some ways to remove viruses from iPhone.
Does A Normal Factory Resetting Remove Virus?
Usually, no. Many users have reported that even after factory resetting their device, the same virus surfaced after a while. There’s a good explanation for this. What happens when you factory reset your iDevice is that all its data gets erased. However, the data erased is not permanent, virus included. Since the virus is not permanently removed, it resurfaces as soon as its fragments are accessed by the iOS system. Sometimes the virus itself is removed, but its traces or fragments remain. Those fragments may include the virus files. Permanently removing the virus and its fragments is the only reliable solution.
Permanently Remove Virus When iPhone Infected with Virus
As mentioned above, simply factory reset iOS is not enough when it comes to removing virus from your iPhone. You need to use a professional data removal tool in order to get rid of it for good. iMyFone Umate Pro is a recommended choice in this regard. This software has been specifically designed to help you erase any kind of data from your iDevice permanently.
iMyFone Umate Pro uses Us.DoD 5220.22-M standard. If a data erasing software uses this standard, then it means it implements advanced three-step data overwriting techniques in order to make sure that the deletion is permanent. So, you are assured that data removed via Umate Pro will never be recovered.
Steps to Remove Virus from iPhone
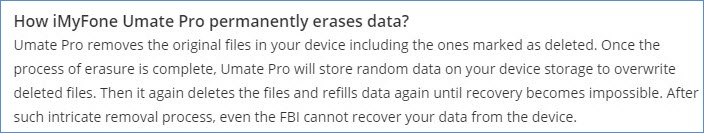
Step 1. Download, install iMyFone Umate Pro on your computer. Plug your iPhone into your computer via a compatible lightning cable.
Step 2. Launch Umate Pro and click on Erase All Data mode from its home interface. Then click the Erase button to proceed.
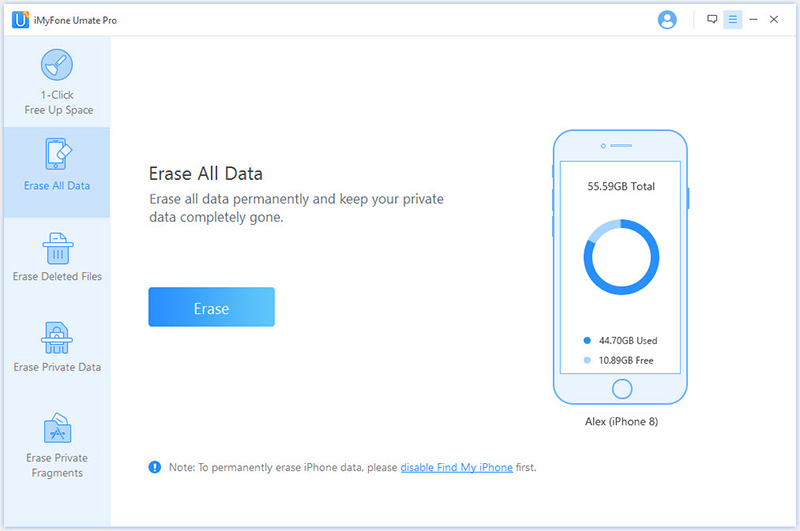
Step 3. On the next screen, choose the Security Level of deletion. Here recommend High Level.
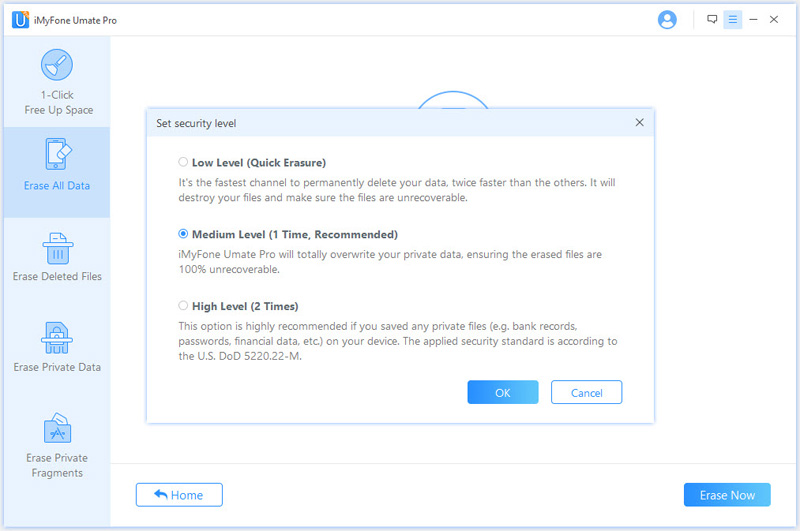
Step 4. Then type ‘delete’ in the provided textbox, start the data deletion process by clicking the Erase Now button.
Other Features
- Optimize iPhone: Optimize your iPhone by erasing junk and temporary files. These files when accumulated, can slow down your device. Umate Pro efficiently cleans them and boosts the device’s performance.
- Manage Storage: Manage your files including photos, apps, large files, etc. efficiently. You can compress large photos, back them up, or delete unwanted files easily via this tool.
- Prevent Privacy Leak: Scan and erase your private files such as call history, contacts, messages, photos, videos, and even third-party app messages permanently to prevent privacy leak.
Examples of iPhone Malware
Although iPhone is rarely infected with malwares, it is not completely invulnerable. Over the years, iOS has been infected with various malwares. Following are some examples of iPhone malware:
#1 Safari JavaScript Pop-up Scareware (March 2017)
This scareware used to abuse pop-up dialogs in Safari browser in iDevices, locking out the user from using the browser. Apple managed to deal with the scareware by making pop-ups in Safari per-tab instead of taking over the entire browser.
#2 AceDeceiver (March 2016)
AceDeceiver is a malware that targets non-jailbroken devices and exploits design flaws in the DRM mechanism of Apple in order to install a malicious app from the App Store.
#3 YiSpecter (October 2015)
YiSpecter targets both jailbroken and non-jailbroken devices. It uses private APIs and performs malicious activities on the infected device. This malware usually gets installed in the form of apps that are signed with enterprise certificates.
#4 AdThief/Spad (March and August 2014)
AdThief/Spad malware targets jailbroken iDevices. It operates by notifying ad developers whether their ads are being viewed, clicked, and/or generating revenue. The malware basically steals small payments away from the developers to the hacker.
#5 AppBuyer (September 2014)
AppBuyer is a dangerous malware that was discovered in September 2014. It connects to C&C server, then downloads and executes malicious executable files on the iDevice. Just like most other malwares, AppBuyer targets jailbroken devices.
#6 Packages by Nobitazzz (August 2012 and September 2013)
Packages by Nobitazzz was an adware that ran ads silently in the background of iOS. The revenue of those ads was sent to the tweak developer. It was reported in August 2012 and analyzed in September 2013.
#7 Find and Call (July 2012)
Also known as FindCall, Find and Call was an app that was later marked as trojan. It automatically uploaded users’ contacts to the company’s server and then sent link to the app to those contacts.
In Conclusion
The above are just a handful of examples. And while none of these were horrific vulnerabilities that could affect every iPhone user, they still show that iOS isn’t impenetrable. So, it's necessary to check whether your iPhone is get injured and remove it from your iPhone.



















 March 12, 2024
March 12, 2024